🏠 Home Infrastructure
One of my favorite and most accessible projects to showcase is my home — which has evolved from a single Dell PowerEdge 2950 into a self-hosted, hybrid cloud production environment.
I’ve designed this setup to support full-scale service deployment, automation, disaster recovery, and an off-site colocation system via S2S VPN. While it began as a homelab, it now operates as a live production environment.
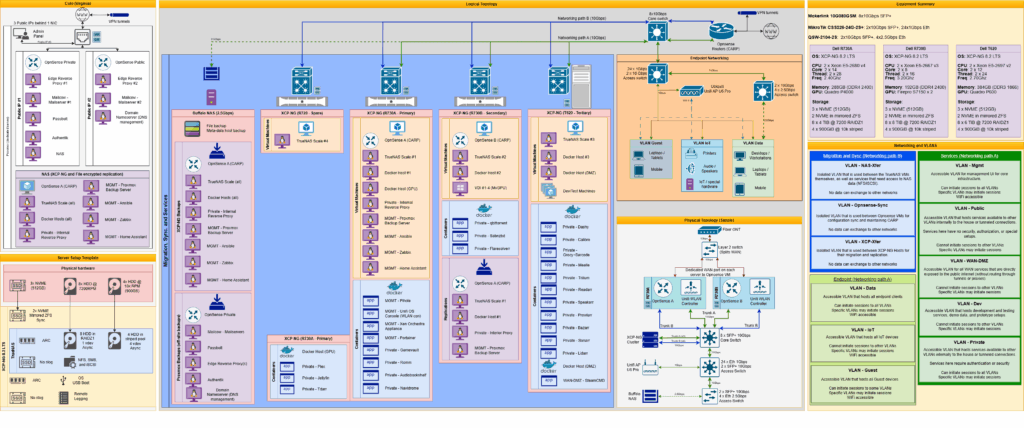
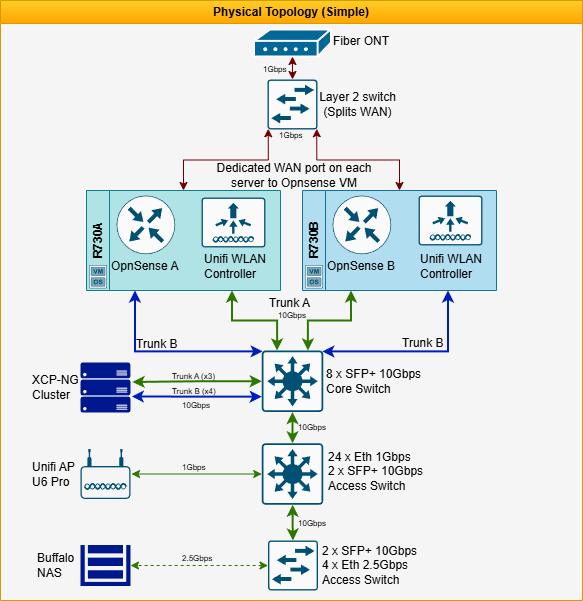
The infrastructure resides in a temperature-controlled room (formerly a coal room) and is built around a rack of four servers: three primary (R730A, R730B, T620) and one backup (R720). The core switching is 10Gbps, with two downstream access switches for endpoints (1Gbps and 2.5Gbps capable).
🌐 Network Topology & Redundancy
-
The fiber ONT terminates into a dedicated L2 WAN switch, which fans out to two primary servers (R730A, R730B).
-
These servers host virtualized OpnSense routers running in CARP (Common Address Redundancy Protocol) to ensure gateway failover.
-
All servers connect to a 10Gbps core switch, which uplinks to two access switches via 10Gbps trunking.
-
Wireless coverage is managed by a UniFi Console WLAN, which manages a UniFi U6 Pro access point.
The network is segmented by performance and security intent:
-
Path A (Endpoint-to-Server): Optimized for external service delivery, local access
-
Path B (Server-to-Server): Optimized for migrations, backups, and internal transfers
🔐 VLAN Segmentation Strategy
| VLAN Category | Subnets | Purpose |
|---|---|---|
| Endpoint Access | Data, IoT, Guest | Client device segmentation with strict ACLs |
| Service Access | Mgmt, Public, Private, WAN-DMZ, Dev | Role-specific isolation for service exposure |
| Backend Sync | NAS-Xfer, Opnsense-Sync, XCP-Xfer | High-throughput traffic (backups, replication) |
This design enables granular access control, security zoning, and performance separation based on workload characteristics.
🖥️ Server & Storage Architecture
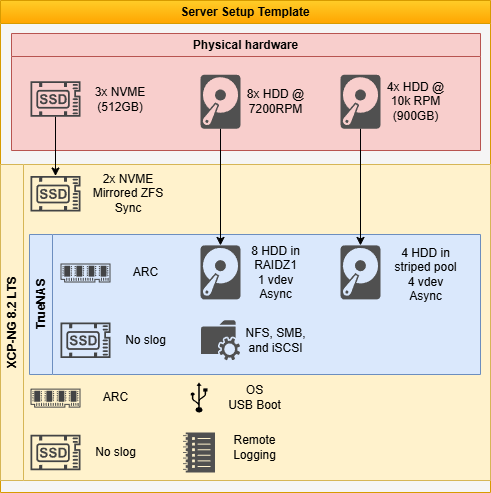
The server infrastructure is designed to support redundancy, performance, and service diversity. Each server is part of an XCP-NG cluster and operates using a shared configuration model for VM templating, backup management, and failover.
The core hardware stack includes:
-
ZFS NVMe Mirrored Pool
-
Operates at the hypervisor level.
-
Hosts all virtual machine OS drives, including TrueNAS VMs.
-
A third NVMe device is installed and available to replace a failed drive.
-
-
8–12 HDD RAIDZ1 Pool
-
Managed via TrueNAS SCALE with direct HBA passthrough from the hypervisor.
-
Stores media, documents, and persistent datasets.
-
Shared back to the XCP-NG cluster and endpoints via SMB, NFS, and iSCSI.
-
-
4-HDD Striped Pool
-
Composed of smaller, high-RPM disks.
-
Used for high-I/O, scratch, and development workloads.
-
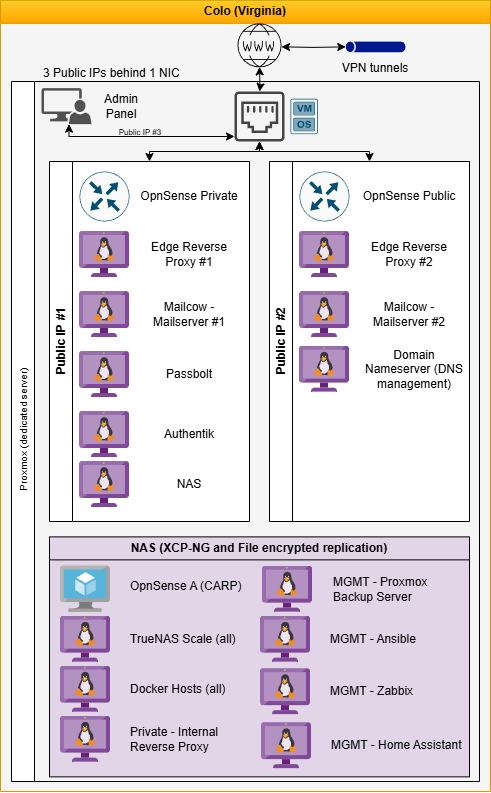
🌍 Colocation Integration
To extend uptime and redundancy, my infrastructure includes a colocated server connected via a persistent Site-to-Site VPN (OpenVPN).
-
The colo server has a single physical NIC but uses virtual MACs to handle multiple public IPs.
-
These are logically segmented into three separate services:
-
An admin panel
-
A private OpnSense router for internal access
-
A public-facing OpnSense router for exposed services
-
Despite sharing physical hardware, internal VLANs and routing rules ensure logical and network isolation between environments.
🛡️ Backup & Redundancy Strategy
Both the home infrastructure and the colocation site perform their own local backups and snapshots. Additionally:
-
Encrypted backups are sent across the VPN tunnel for off-site redundancy.
-
Each XCP-NG host performs VM metadata and config backups to a local Buffalo NAS.
-
Key VMs receive secondary backups to remote storage.
-
The shared configuration model allows cross-server VM restoration in the event of hardware failure.
This platform allows me to develop, test, and operate infrastructure at an enterprise scale while retaining full control of the environment. I rely on this setup for both personal productivity and professional demonstration, and I continuously iterate on its capabilities based on real-world usage and performance evaluation.
⚙️ Service & Automation Layer
This infrastructure supports a wide range of internal and external services, including:
-
Home automation
-
DNS filtering and split-DNS resolution
-
Media management
-
Mail Servers, Password managers, Cloud storage
-
Smart device control
-
Endpoint configuration and lifecycle automation
-
Remote VPN access
All services are deployed using template-based provisioning with automation tasks integrated via Ansible and systemd timers.